When asked for a good source to learn how to write BPF code I send people to the BPF Compiler Collection (BCC) project - https://github.com/iovisor/bcc . In addition to a C/C++ library for BPF and bindings in Python and LUA, it contains various tracing tools with clear examples of how to use them. It’s useful to read the source of those tools to learn the coding patterns with BPF.
A number of the gadgets in Inspektor Gadget such as execsnoop and opensnoop are directly based on BCC tools execsnoop and opensnoop without modifications. In this case, Inspektor Gadget provides the high-level kubectl-like user experience: users don’t have to install BCC on the nodes, no need to ssh into the nodes, and they can use high level concepts like Kubernetes labels to filter the traces.
Last month, BCC gained a new tracing tool:
bindsnoop
. It traces the kernel
function performing socket binding. It allows users, for example, to see that
nginx binds on TCP port 80. Thus, we wanted to integrate bindsnoop into a
Inspektor Gadget gadget in order to help debug why connections might fail. In
order to make integrating new BCC tools into Inspektor Gadget, we introduced a
new --cgroupmap option into BCC that allows for filtering by
cgroups
.
With this change, BCC tools can be integrated seamlessly into Inspektor Gadget.
Indeed, bindsnoop was integrated with only
a few lines of
code
.
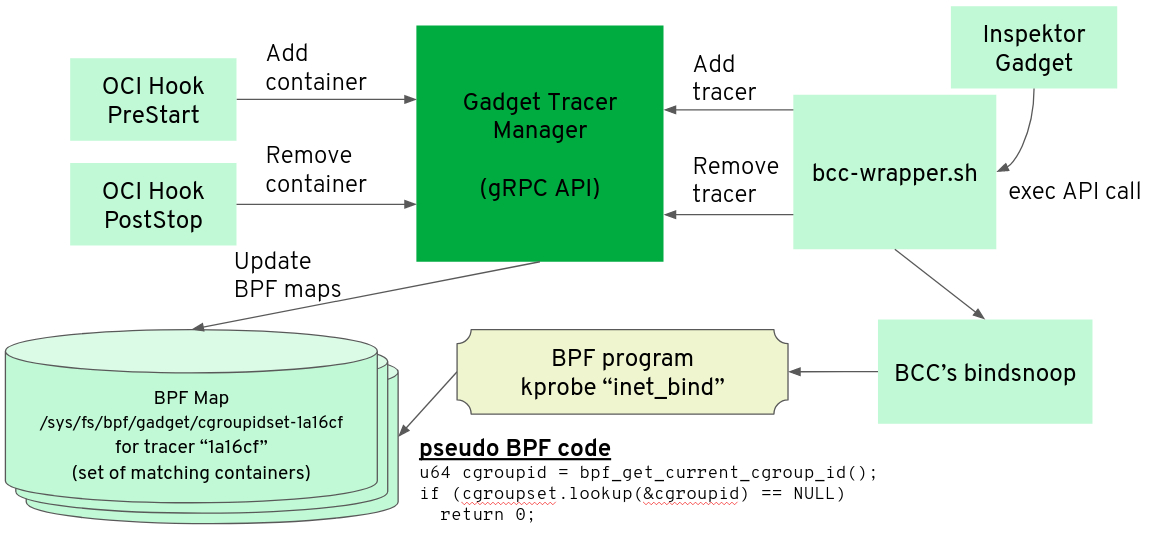
How it works
The Gadget Tracer Manager is a daemon deployed as a DaemonSet that keeps track of the gadgets currently running in Inspektor Gadget (such as bindsnoop or execsnoop) and the containers running on each node. When the user starts a new instance of gadget like bindsnoop, the Gadget Tracer Manager populates a BPF map with the set of cgroup ids of containers that should be traced by that gadget.
Conclusion
It’s become easier to add new gadgets in Inspektor Gadget thanks to BCC. As an Open Source project, contributions are welcome. Join the discussions on the #inspektor-gadget channel in the Kubernetes Slack or, if you want to know about our services related to BPF and Kubernetes, reach us at [email protected] .


